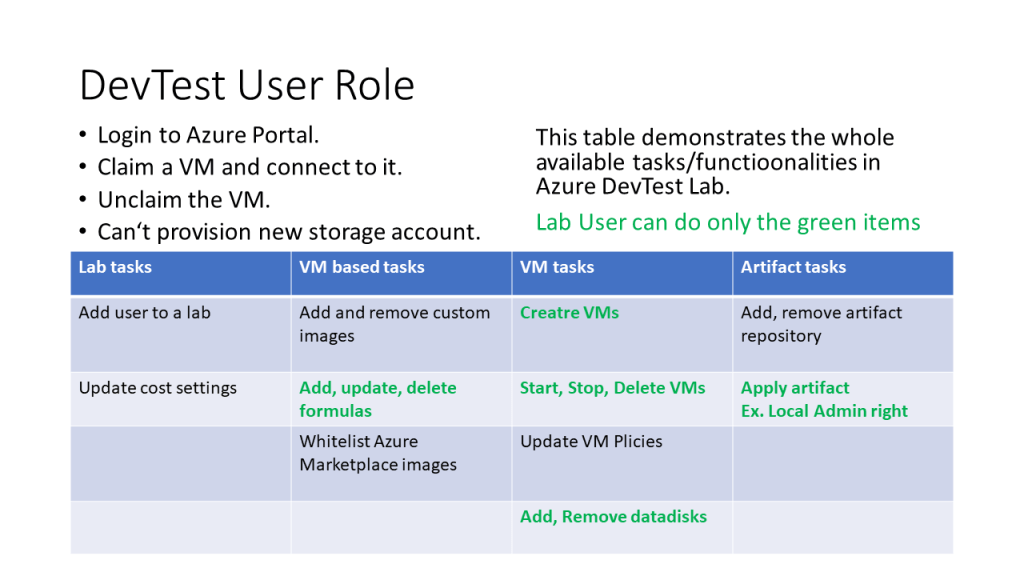
The Azure Virtual Network (VNet) is like a container that provide traffic isolation and segmentation.
An Azure virtual network (VNet) is a representation of your own network in the cloud. You can control your Azure network settings and define DHCP address blocks, DNS settings, security policies, and routing. You can also further segment your VNet into subnets and deploy Azure IaaS virtual machines (VMs) and PaaS role instances, in the same way you can deploy physical and virtual machines to your on-premises datacenter. In essence, you can expand your network to Azure, bringing your own IP address blocks.
The termes which are used in VNet are as follows:
- Virtual Network
- Virtual Network Subnet
- Gateway Subnet
- Virtual Network Gateway
- Viurtual VPN Gateway
- Network Security Group (NSG) -> Can be assigned to
- Virtual Network
- Virtual Machine
- Sunbet -> at subnet level would be prefered.
- User Defined Routing (UDR) -> for customizing traffic.
We can have one to many VNets but of course there’s subscription limitation. All VNets are isolated boundries. But there’s different types of connectivity available between VNets according to the scenario.
Connectivity types
| VNets Peering | There’s two different VNets peering: – Global Peering – VNets Peering -> the VNets must be in the same region. |
| VPN Gateway/ Tunnel | The VPN Gateway is used for different types of connectivity: – VNet-to-VNet (Microsoft Doc) – Site-to-site -> On-premises env to Azure VNet (Microsoft Doc) – Point-to-site -> Laptop to Azure VNet |
| Express Route |
Virtual Network Security
Provide network security with using
- Network security group
- Using attack simulation to access protection and detection capabilities of azure web application firewall (WAF)
Network Security Group (NSG)
The Network Security is applied to the network via Network Security Groups (NSGs) and it has the following features:
- It has a stateful firewalll for inbount and outbound traffic.
Clouds: Virtual Network and Subnet
Web Application Firewall (WAF)
Common vulnerabilities [more]
- Injection
- Broker authentication
- Cross-site scription (xss)
- Sensitive Data Exposure
- Insecure Deserlialization
- Broker Access Control
- Insufficient logging and monitoring
- Server-side Request Forgery (SSAF)
- Known Vulnerabilities
- Security Misconfiguration
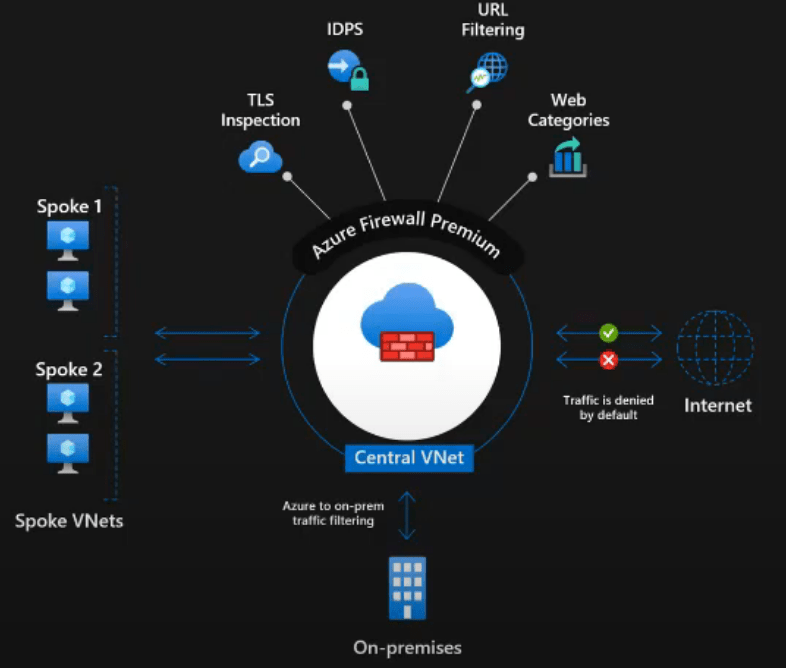
Central DNS Management and Logging with Azure Firewall
Azure Firewall overview [Source]
Firewall as a Service is a PaaS.
| Azure Firewall | |
|---|---|
| Central governance of all traffic flows | – Built-in high availability and auto scale – Network and application traffic filtering – Centralized policy across VNets and subscriptions |
| Complete VNET protection | Filter Outbound, Inbound, Spoke-Spoke and Hybrid Connections traffic (VPN and ExpressRoute) |
| Centralized logging | Archive logs to a storage account, stream events to your Event Hub, or send them to Log Analytics or Security Integration and Event Management (SIEM) system of choice. |
| Best for Azure | DevOps integration, FQDN tags, Service Tags, Integration with ASE, Backup and other Azure Services. |
| Azure Firewall Premium | Next-Gen Firewall features, including TLS inspection, IDPS, and URL Categories. |
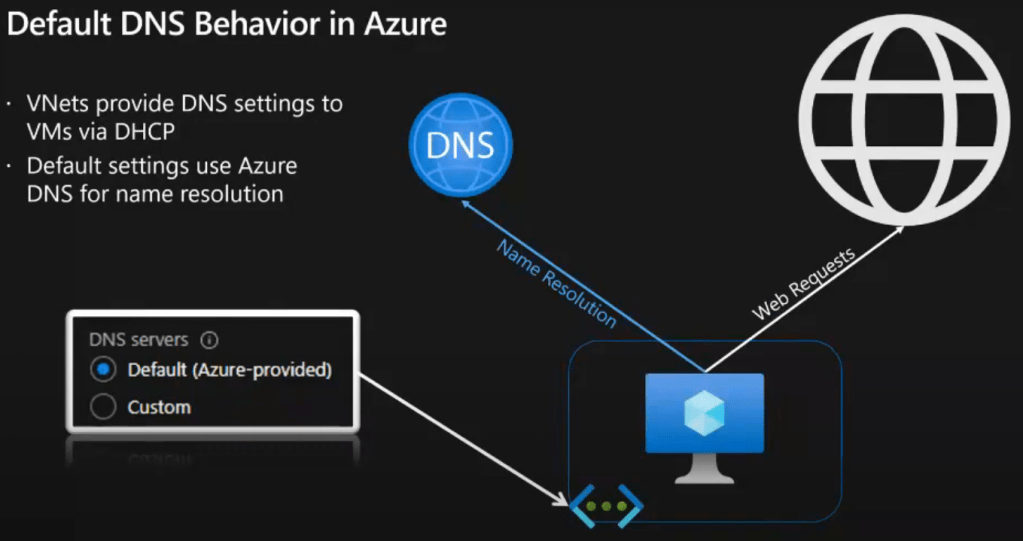
Default DNS behavior in Azure [Source]
- VNets provide DNS settings to VMs via DHCP
- Default settings use Azure DNS for name resolution
Azure Firewall DNS Proxy and custom DNS