
Topices
Advantages of the Azure Active Directory
- It’s suitable for the cloud.
- Support modern authentication protocols. (e.g. WS-FED, SAML Federation, OpenID Connect, OAuth)
- Azure AD will come with SDKs like ADAL and MSAL.
- Azure AD supports the scenarios like B2C, B2B, B2E (employee) and Software As a Service (SaaS) applications.
Hybrid Active Directory (On-Prem & Cloud)
- The on-premises identities can be synced to the Cloud via Azure AD Connect Tool.
- Even Multiple forests can be synced.
- The authentication can be federated to the on-premises with (ADFS).
- The identity can be manged in Azure AD but authentication can be done by on-prem AD server.
- The on-prem group policies can be synced in Azure AD.

Hybrid identities
- Create a new active directory on Azure
- Organization name: where we want to reference e.g. <MY_ORG>.local
- Initial domain: <MY_ORG>.onmicrosoft.com
- name, country, region
- Add e.g. <MY_DOMAIN_NAME>.com as a new domain name for the <MY_ORG>.onmicrosoft.com
- Verify the ownership of the domain name by adding a TXT record to the DNS Server
- Add UPN suffix to the on-prem forest. Server > Tools > Active Directory Domain and trusts > Right click Active Directory Domains > Properties > Alternative UPN Suffix > Add <MY_DOMAIN_NAME>.com
- Go to users on on-prem AD and change the domain to alternative domain or using powershell via Get-ADUser and Set-ADUser commands.
- For hybrid identities we use Azure AD Connect.
- We need a Global Admin Account in AAD.
- Download and install Azure AD Connect on the on-prem AD Server.
Provisioning a Azure Active Directory
Create Azure Active Directory (Azure Portal > All Services > Create button > the following image)

Azure Active Directory’s blade overview

Users
Groups
Enterprise applications: add new SaaS applications like Box, Dropbox,…
Devices: to mange devices.
App registration: Register application to machine to machine communication / client credential flow [more].
Application proxy: for exposing on-premises.
Azure AD Connect: for sync with on-prem Active Directory to AAD for hybrid identity.
App registration
App registration blade features are:
- New Registration
- Endpoints
- Troubleshooting
- Listing the registered applications ( All Applications | Owned Applications)

New Registration

Web APP/API is like a web site. The URL infront of Web APP/API (REST API) is the Sign-on URL. Ex. http://localhost:5000/signin-oidc
Native is like mobile app, desktop application or javascript single-page application. Redirect URL is where Azure AD directs the authenticated user’s details.
After the app registration, the following items can be important for developers. They are always available on the registered app blade.
- Application or client ID via Overview blade
- Redirect URL after successful authentication via Authentication blade
- Logout URL via Authentication blade
How to go the registered app blade
AAD > App registration> select & click the registered
Application/ Client ID

Redirect URL after successful authentication

Logout URL

App Registration usages
- For developing the Client Credential Flow / Machine to Machine communication
- For login to Azure API Management’s Developer Portal with AAD/ AAD B2C identity
Conditional Acess Policy
Licenses
Required license for conditional access policy
- Azure AD Premium P1 license
- Microsoft 365 Business Premium licenses
Conditions
The conditional access policy uses the Sign-in Risk value (it’s a probability). But it’s not the only value. Based on the policies different probability values have to be calculated [more]. Based on how conditions are configured different values are calculated and used.
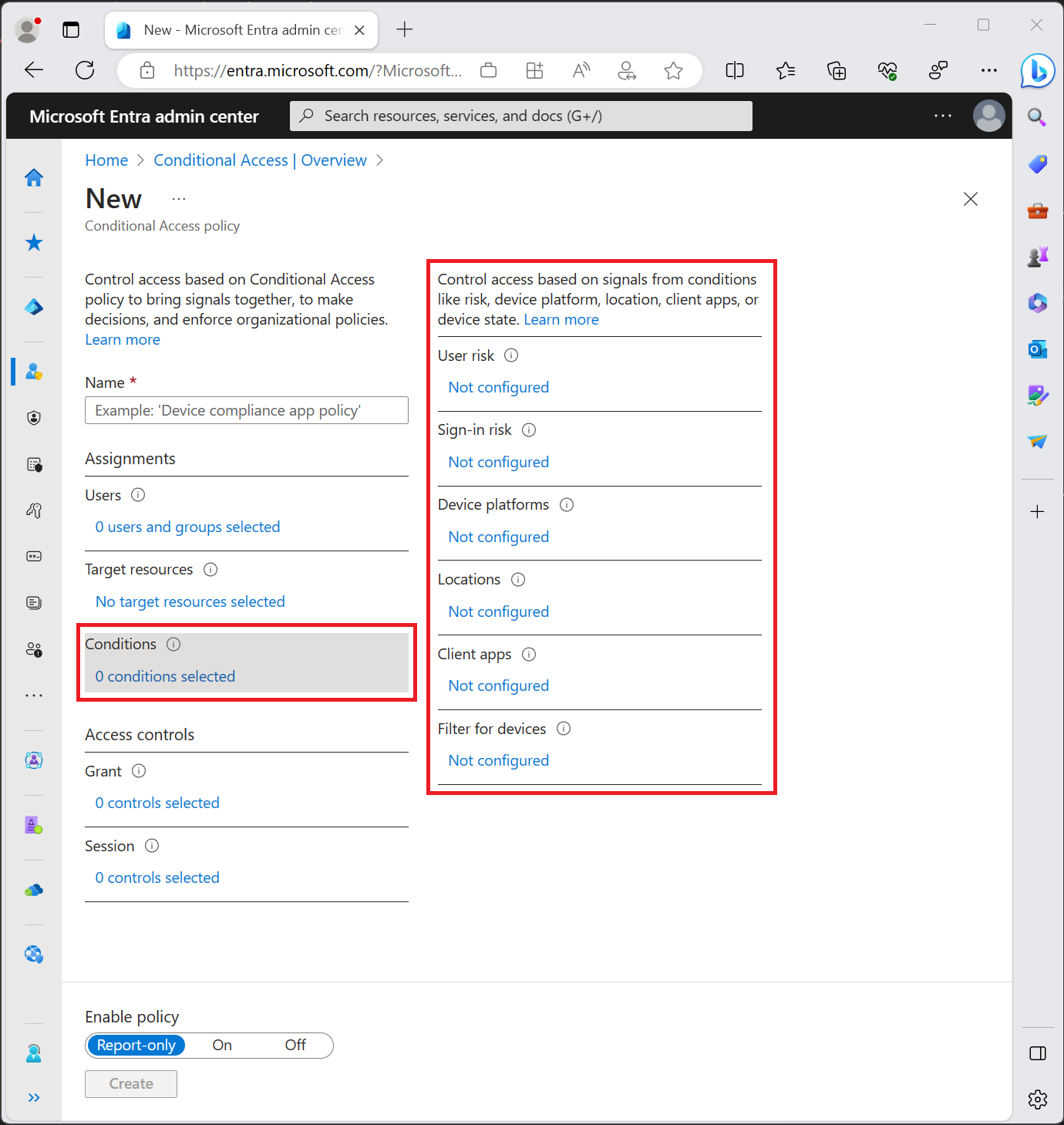
Grant
In Grants either you block the users who have the conditions or you grant then if one of the checkboxes is available. Multi-factor is available only in the following licenses but with some differences [more]:
- Microsoft 365 Business Premium and EMS or Microsoft 365 E3 and E5
- Azure AD Premium P1
- Azure AD Premium P2
- All Microsoft 365 plans
- Azure AD free

Report-only mode [more]
Report-only mode is a new Conditional Access policy state that allows administrators to evaluate the impact of Conditional Access policies before enabling them in their environment. With the release of report-only mode:
- Conditional Access policies can be enabled in report-only mode.
- During sign-in, policies in report-only mode are evaluated but not enforced.
- Results are logged in the Conditional Access and Report-only tabs of the Sign-in log details.
- Customers with an Azure Monitor subscription can monitor the impact of their Conditional Access policies using the Conditional Access insights workbook.

Source : https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
Self-Service Password Reset
You owe your dreams your courage.
Koleka Putuma
2 thoughts on “Onboarding : Azure Active Directory”