
Topics
- Keywords
- Monitoring concepts
- Available monitoring options
- Azure Monitor agents
- Azure Diagnostics Extension
- Azure Log Analytics Agent
- Windows Agents
- Linux Agents
- Dependancy Agent
- Azure Monitor Log
- Monitoring Best Practices
- Azure Security Center
- Azure Activity Log
- Benefit of connecting Activity Log to Log Analytics
- Connect an Activity Log to a Log Analytics workspace
- Resource Management
Related topics
Scenarios
- Monitoring resources
- Managing resources via
- Resources groups
- Tags
- Policies
- RBAC
Extension compured to agent
Extensions have to be installed to manage agents whenever possible.
Log Analytics extension for windows and linux installs the log analytics agent on azure vm. Azure monitor dependancy extension for windows and linux installs dependancy agent on azure vm.
Keywords
- Azure Monitor
- Azure disgnostic extension
- Azure log analytics agent
- Windows agents
- Linux agents
- Telegraf agent
- Dependency agent
- Resource Management
- Resource group
- Tag
- Policy
- RBAC
Azure Security Center
Source
Azure Activity Log
- activity log is an insight into subscription-level events (Retention period of 90 days)
- each resource has its own activity log, that is a part of subscription-level activity log
- each resource activity log can be connected to only one log analytics workspace
- one log analytics workspace can be connected to the activity log of multiple subscriptions in a same tenant.
Connect Activity Log to Log Analytics Workspace
Select Log Analytics Workspace > Azure Activity Log / VM / Storage/.. menu > Select Resource / subscription > Connect / disconnect

Benefit of connecting Activity Log to Log Analytics
- consolidate the activity logs of multi subscriptions in one place for analysis.
- Store Activity Log enteries for more than 90 days.
- Correlate Activity Log data with Azure Monitor data.
- Use Log queries for complex analysis and get deep insight on Activity log.
Note
Each subscription has only one Activity Log.
Each Activity Log can be connected to only one Log Analytics Workspace.
One Log Analytics Workspace can be connected to the Activity Log of multiple subscription in a same tenant.
Connect an Activity Log to a Log Analytics workspace
Variante 1 (form log analytics blade)
Go to the Log Analytics Workspace > Select one of the created workspaces > From the blade > Azure Activity Log > Select one Subscription > Connect | Disconnect
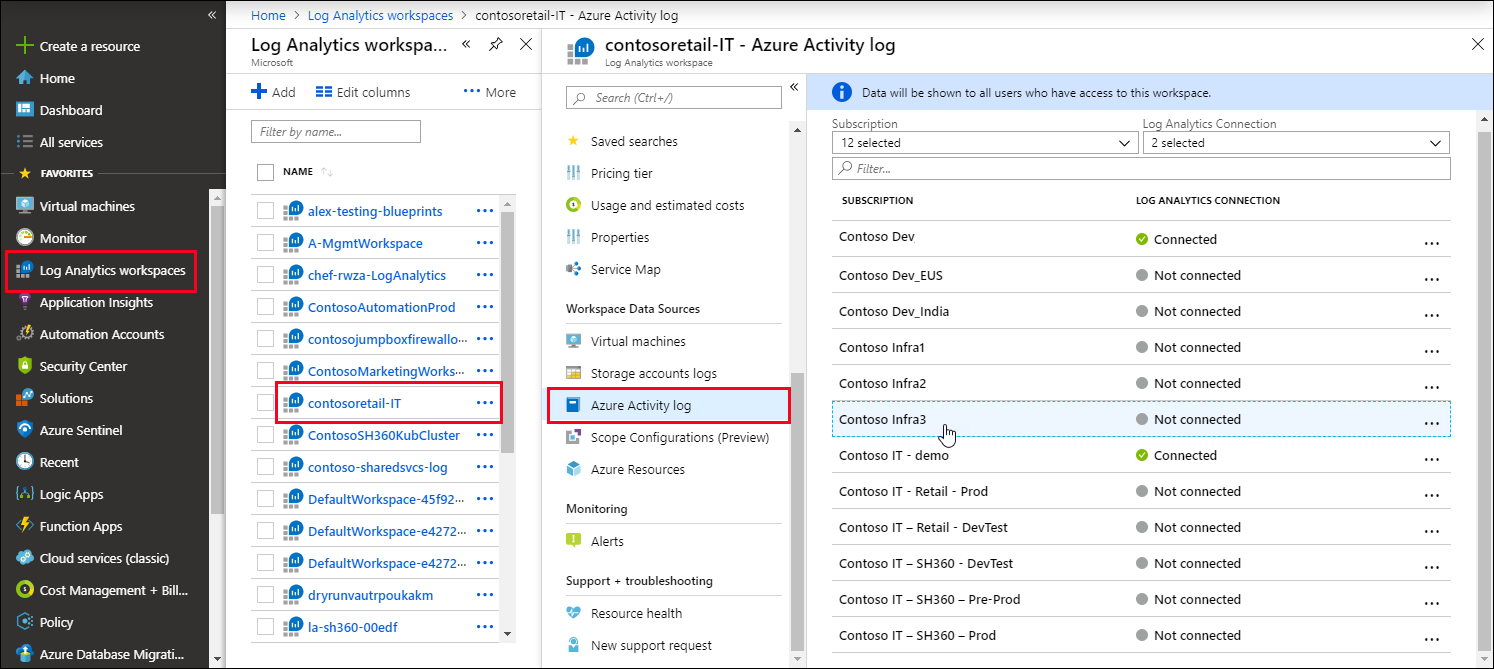

Variante 2 (from activity log blade)
Select a resource > Select Logs / Diagnostic settings menu > Select a Log Analytics Workspace.
Source
Resource Management [source]
Scenario: Company has been moving to the cloud. This movement happened organically across different departments, and resulted in a lack of awareness of what’s already been created and where everything is. There’s no ability to easily determine who owns which resources. There’s no enforcement of standards for things like resource names, resource sizes, and geographic locations. There’s also been several instances where critical resources were inadvertently deleted, causing business-critical outages.
- Protect business critical resources against deletion
Resource group [source]
- logical container for resources
- Resources can be a member of just one resource group
- Many resources can be moved between resource groups
- Resource group can not be nested
- Life cycle: By deleting a resource group all its resources are deleted as well e.g this kind of life cycle is useful for non-production
- Authorization: a scope for applying role-based access control (RBAC) permissions
- Creation: cli, powershell, portal, template, Azure SDK
- Naming convention: using descriptive names e.g. [project-id]-[region]-[dev|prod|qa|test]-[rg]
Resource tag [Source]
- for better organization
- name/value pairs of text
- department : finance
- environment : dev
- cost center : 76ZS3
- Project-id : sample
- tags can be used for life cycle e.g. to shutdown vms
- each resource max 50 tags
- name limited to 512 character for all resources, except storage 128
- tag value 256 character
- tags are not inherited from parent
- not applied to all resources
- cli, powershell, portal, REST API
- use Azure Policy to automatically add or enforce tags for resources your organization creates based on policy conditions that you define -> via making a tag mandatory
az resource tag --tags Department=Finance \
--resource-group msftlearn-core-infrastructure-rg \
--name msftlearn-vnet1 \
--resource-type "Microsoft.Network/virtualNetworks"
Policy
- The Azure Policy is used to manage and governe the infrastructure, refer to Onboarding : Azure Infrastructure document.
- to force standards
- These policies apply and enforce rules that your resources need to follow.
- These policies can enforce these rules when resources are created, and can be evaluated against existing resources to give visibility into compliance.
- can enforce things such as only allowing specific types of resources to be created
- or only allowing resources in specific Azure regions.
- You can enforce naming conventions across your Azure environment.
- enforce that specific tags are applied to resources
- your infrastructure stays compliant with your corporate standards, cost requirements, and any service-level agreements (SLAs) you have with your customers.
- with policies the costs can be managed
- the allowed vms can be managed
- the allowed region can be managed
- SKUs can be managed
- policy definition is json. There are hundreds of samples available on GitHub.
- organize policies with initiatives
- Managing a few policy definitions is easy, but once you have more than a few, you will want to organize them. That’s where initiatives come in.
- Initiatives work alongside policies in Azure Policy
- An initiative definition is a set or group of policy definitions to help track your compliance state for a larger goal.
- Like a policy assignment, an initiative assignment is an initiative definition assigned to a specific scope
- Initiative assignments reduce the need to make several initiative definitions for each scope.
- This scope could also range from a management group to a resource group.
RBAC focuses on user actions at different scopes. Azure Policy focuses on resource properties during deployment and for already-existing resources. Unlike RBAC, Azure Policy is a default-allow-and-explicit-deny system.
{
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachines"
},
{
"not": {
"field": "Microsoft.Compute/virtualMachines/sku.name",
"in": "[parameters('listOfAllowedSKUs')]"
}
}
]
},
"then": {
"effect": "Deny"
}
}
# Apply an Azure policy
# Register the resource provider if it's not already registered
Register-AzResourceProvider -ProviderNamespace 'Microsoft.PolicyInsights'
# Get a reference to the resource group that will be the scope of the assignment
$rg = Get-AzResourceGroup -Name '<resourceGroupName>'
# Get a reference to the built-in policy definition that will be assigned
$definition = Get-AzPolicyDefinition | Where-Object { $_.Properties.DisplayName -eq 'Audit VMs that do not use managed disks' }
# Create the policy assignment with the built-in definition against your resource group
New-AzPolicyAssignment -Name 'audit-vm-manageddisks' -DisplayName 'Audit VMs without managed disks Assignment' -Scope $rg.ResourceId -PolicyDefinition $definition
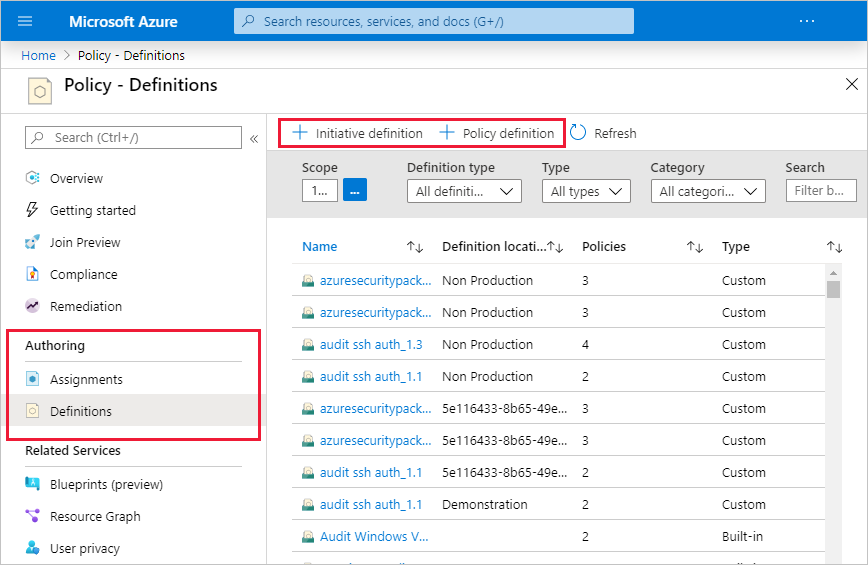
Here are some of the most common policy definitions you can apply.
| Policy definition | Description |
|---|---|
| Allowed Storage Account SKUs | This policy definition has a set of conditions/rules that determine whether a storage account that is being deployed is within a set of SKU sizes. Its effect is to deny all storage accounts that do not adhere to the set of defined SKU sizes. |
| Allowed Resource Type | This policy definition has a set of conditions/rules to specify the resource types that your organization can deploy. Its effect is to deny all resources that are not part of this defined list. |
| Allowed Locations | This policy enables you to restrict the locations that your organization can specify when deploying resources. Its effect is used to enforce your geographic compliance requirements. |
| Allowed Virtual Machine SKUs | This policy enables you to specify a set of VM SKUs that your organization can deploy. |
| Not allowed resource types | Prevents a list of resource types from being deployed. |
| Parameter | Description |
|---|---|
| Name | The actual name of the assignment. For this example, audit-vm-manageddisks was used. |
| DisplayName | Display name for the policy assignment. In this case, you’re using Audit VMs without managed disks Assignment. |
| Definition | The policy definition, based on which you’re using to create the assignment. In this case, it’s the ID of policy definition Audit VMs that do not use managed disks. |
| Scope | A scope determines what resources or grouping of resources the policy assignment gets enforced on. It could range from a subscription to resource groups. Be sure to replace <scope> with the name of your resource group. |
Source
Management Group
- Azure Management Groups are containers for managing access, policies, and compliance across multiple Azure subscriptions.
- Management groups allow you to order your Azure resources hierarchically into collections, which provide a further level of classification that is above the level of subscriptions.
- All subscriptions within a management group automatically inherit the conditions applied to the management group.
- Management groups give you enterprise-grade management at a large scale no matter what type of subscriptions you might have.
- Management Group security policy cannot be altered by the resource or subscription owner allowing for improved governance.
- Another scenario where you would use management groups is to provide user access to multiple subscriptions
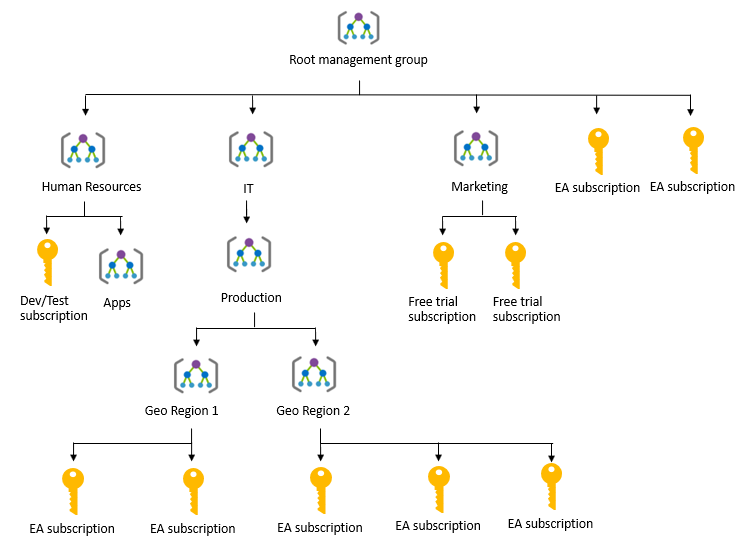
- You can manage your Azure subscriptions more effectively by using Azure Policy and Azure role-based access controls (RBACs). These provide distinct governance conditions that you can apply to each management group.
- create management group by using cli, powershell, portal


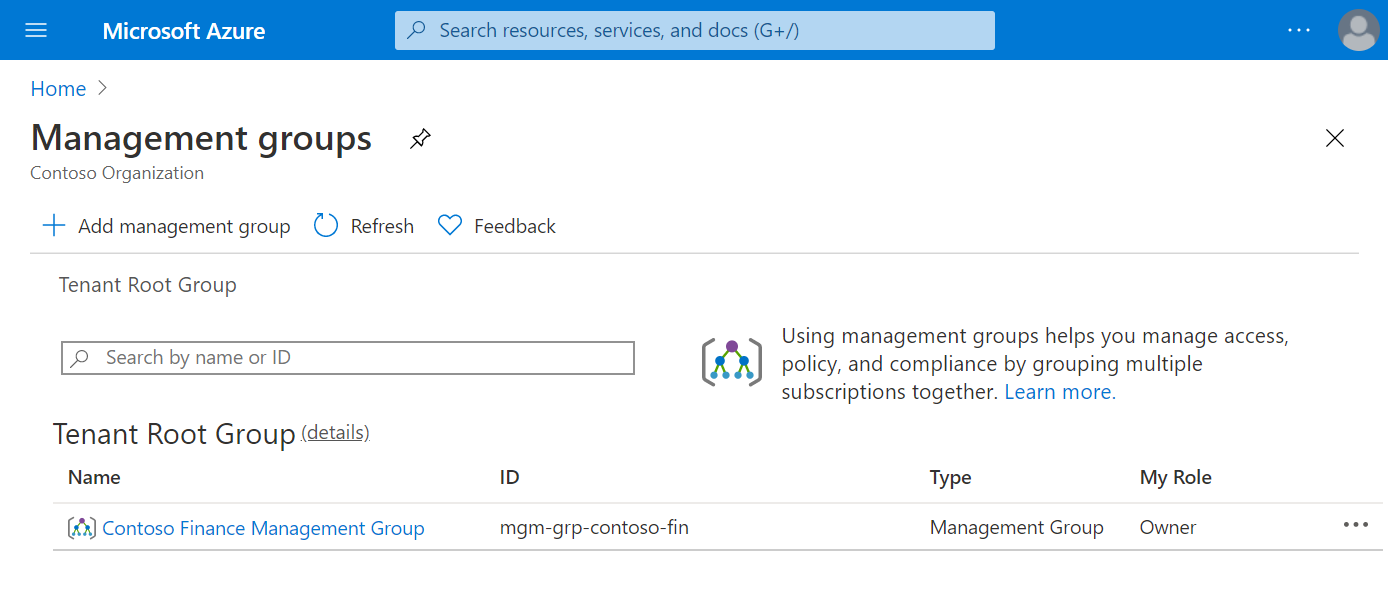
- Root management group
- After you select Save on your first management group, a root management group is created in the Azure Active Directory (Azure AD) organization.
- By default, the root management group’s display name is Tenant root group.
- The ID is the Azure AD ID.
- After this group is created, all existing subscriptions in the Azure AD organization are made children of the root management group.
- The management group you create appears under the Tenant root group.
- Any Azure AD user in the organization can create a management group. The creator is given an Owner role assignment.
- A single Azure AD organization can support 10,000 management groups.
- A management group tree can support up to six levels of depth not including the Root level or subscription level.
- Each management group can have many children.
- When your organization creates subscriptions, they are automatically added to the root management group
Source
Azure Blueprints
- Azure Blueprints is a declarative way to orchestrate the deployment of various resource templates and other artifacts, such as:
- Role assignments
- Policy assignments
- Azure Resource Manager templates
- Resource groups
- With Azure Blueprint, the relationship between the blueprint definition (what should be deployed) and the blueprint assignment (what was deployed) is preserved.
- This connection supports improved deployment tracking and auditing.
- The Azure Blueprints service is backed by the globally distributed Azure Cosmos database.
- Blueprint objects are replicated to multiple Azure regions.
- This replication provides low latency, high availability, and consistent access to your blueprint objects, regardless of which region Blueprints deploys your resources to.
- With Blueprints, the relationship between the blueprint definition (what should be deployed) and the blueprint assignment (what was deployed) is preserved. This connection supports improved tracking and auditing of deployments. Blueprints can also upgrade several subscriptions at once that are governed by the same blueprint.
Source
Compliance Manager
- Governing your own resources and how they are used is only part of the solution when using a cloud provider.
- Microsoft takes this management seriously and provides full transparency with four sources:
- Microsoft Privacy Statement
- Microsoft Trust Center
- Service Trust Portal
- Compliance Manager
Source
Role-based access control (RBAC)
Source
You owe your dreams your courage.
Koleka Putuma