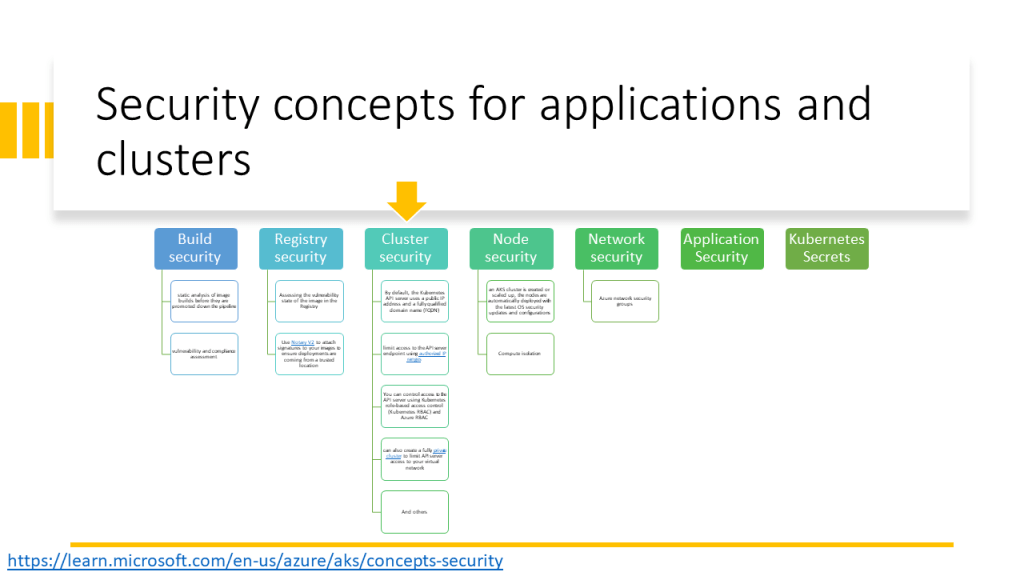
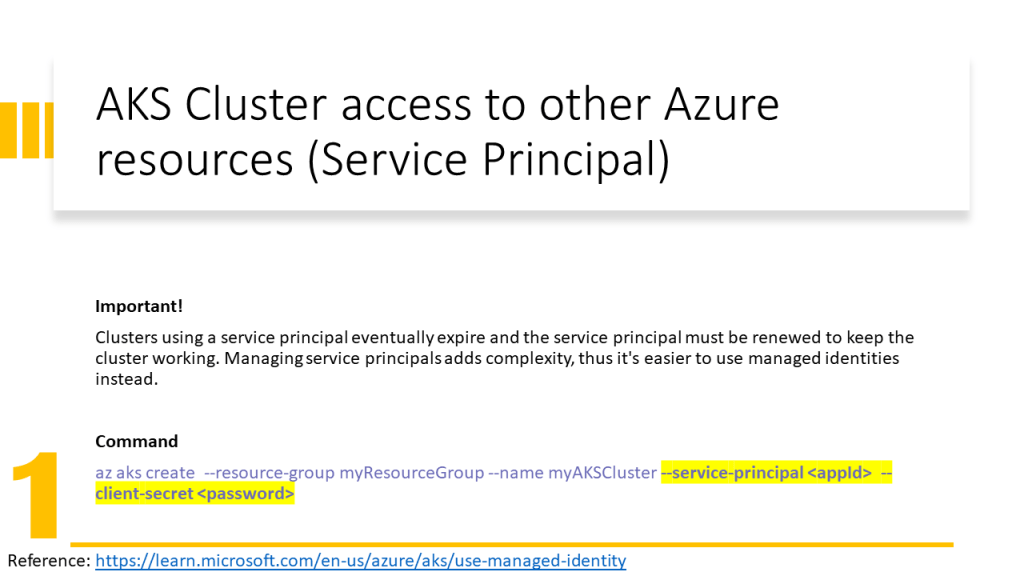
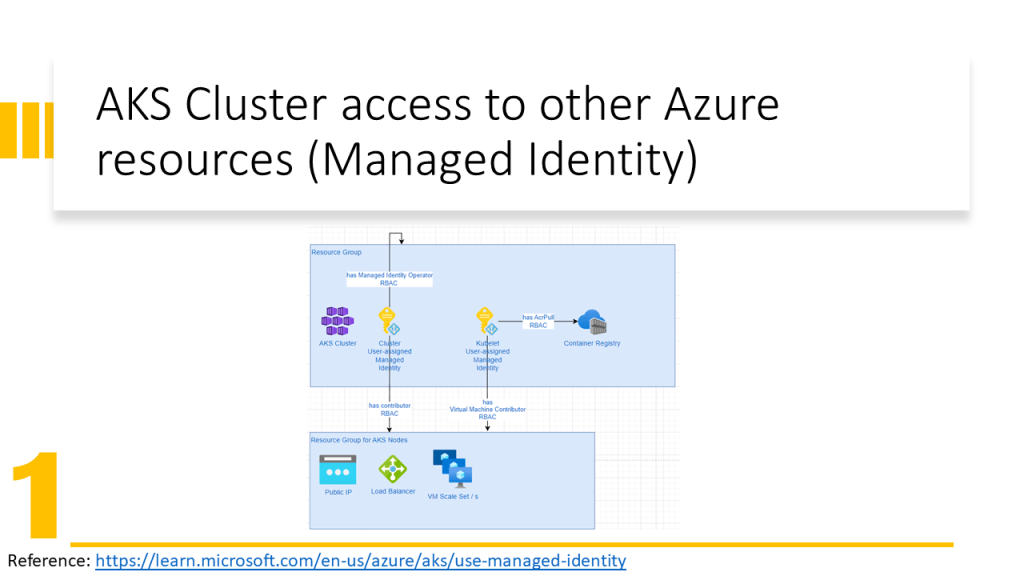
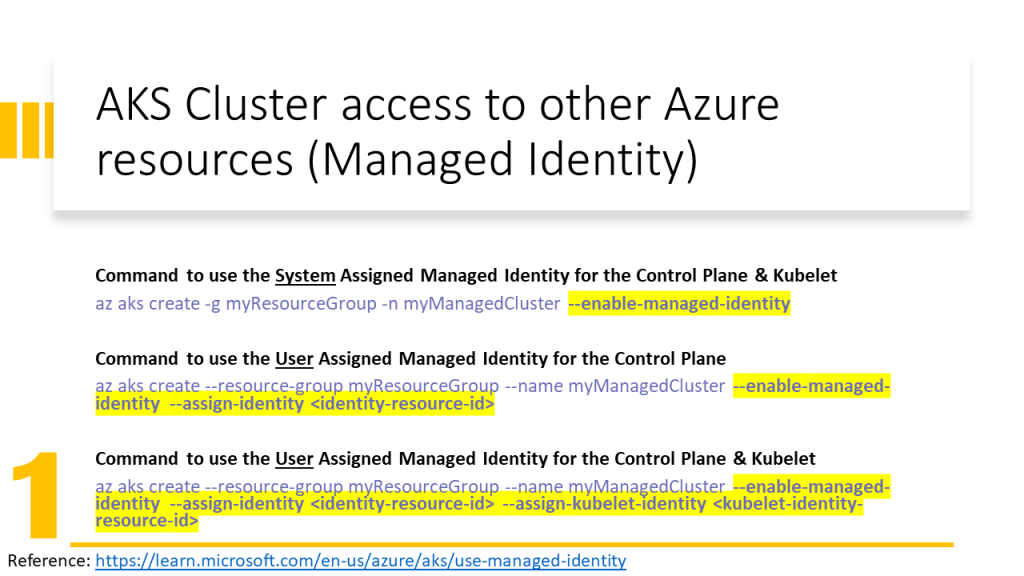
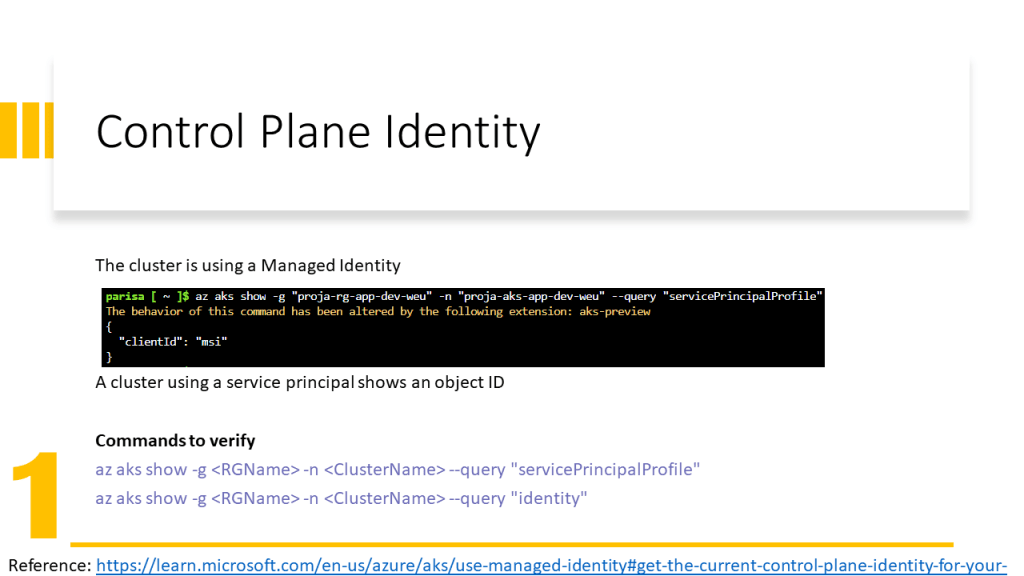
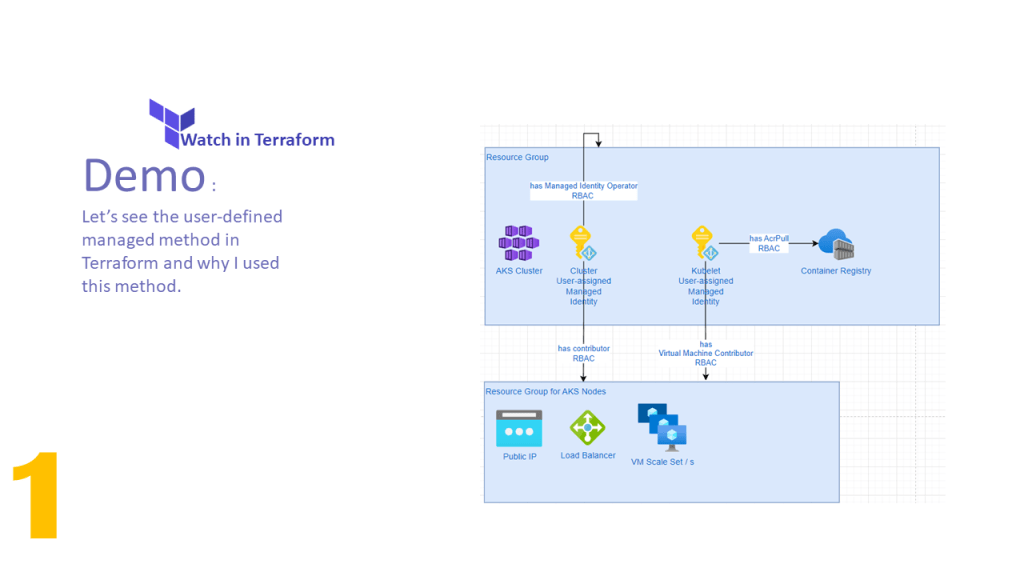
This document also explains how to prepare the environment in the GitHub Codespace instead of using the local machine. However, this technique can be used on local machines as well.
Install Terraform cli in GitHub Codespace by using the dev container
We use Terraform to deploy GCP resources. I used the GitHub workspace. In the GitHub workspace, I have used the Dev container to install Terraform cli in the environment. The figure below shows the dev configuration for installing the latest Terraform cli.

Configure SSL in GitHub Codespace
Configure the SSL key in GitHub Codespace to push the code to the repository. This method works only for cloning with ssh.

I have used these GitHub Docs for the following steps:
Create a project in GCP
This is mandatory to have a project in GCP. The important is to know, that the project-id can never be changed after creation.

Creating a Service Account to use for Terraform deployment
Follow the steps below to create a service account for deploying GCP resources via Terraform. Terraform uses this account to authenticate.

The next is creating a key. Select the created service account and go to Manage Keys to generate a key.

Change to KEYS tab and by using Add Key button select Create new key item.

We should select a format for the new key. I used the JSON. I want to download the key as JSON and use it as a credential file.

After downloading the JSON file, I renamed it to credentials.json. and copied it to my development environment. Be careful not to push this file into the repository.
Provide credentials for Terraform
We have two options:
Option 1: Create an environment variable that contains the path to the credentials file.
export GOOGLE_APPLICATION_CREDENTIALS="./credentials.json"Option 2: configure the credentials in Terraform google resource.
provider "google" {
project = var.gcp_project
region = var.location
credentials = "/workspaces/codespaces-blank/credentials.json"
}